|
|
3 years ago | |
|---|---|---|
| .. | ||
| audit | 4 years ago | |
| README.md | 3 years ago | |
| scan1.png | 4 years ago | |
| scan2.png | 4 years ago | |
README.md
scan
You're going to do like Trinity in the movie The Matrix Reloaded. Except that you're not going to turn off the electricity in a city, and you probably don't wear as much leather, but that's okay.
By design and by default, most network entities have a high discoverability.
Whatever your motivations for exploring a network (hacking, curiosity...), you generally proceed in this order :
- Scan a network to find hosts
- Scan a host to get information (hardware, OS & exposed services)
1. can be done by analyzing the link layer of Internet protocols, in particular ARP in order to gather MAC addresses (the identifier of a network interface, such as Wi-Fi or Ethernet cards).
2. is usually performed by analyzing the network and transport layers, in particular the IP & TCP protocols with the nmap tool.
For the context, when you open a website, here are the protocols involved, from the highest to lowest level (the protocols at the top depend on those at the bottom):
HTTP: application layer (website data) - messagesTLS: application layer ("lock" sign) - secure connectionTCP: transport layer (port number) - reliable connectionIP: network layer (IP address) - global communicationARP: link layer (MAC address) - local communication
For this challenge, you will focus on IP, ARP & TCP, and therefore on IP/MAC addresses and ports.
You will need to add these 2 VM :
You will only have control over "laptop". A port forwarding is set on 10122 so you can connect through SSH, the password is a single space.
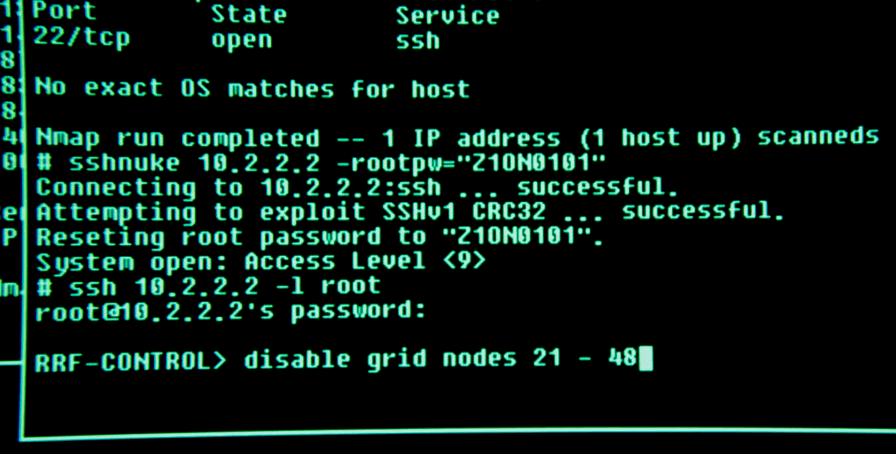
Your mission, should you choose to accept it, is to scan the network interface enp0s8 and find a way in the server, you will know you have succeeded when you see :
RRF-CONTROL> █
Because the VirtualBox Internal Network is very slow (10 Mbps, Ethernet is usually 1000 Mbps), expect long scan times :
- ARP scanning takes up to 5 minutes
- port scanning takes up to half an one hour with the option
-T4(even more without).
May the Fourth be with you.
Another depiction of the
nmaptool: in Ocean's 8, Rihanna uses Kali Linux to steal a valuable diamond.Same strategy, different styles